The form’s action is pretty self explanatory, but how does it work?
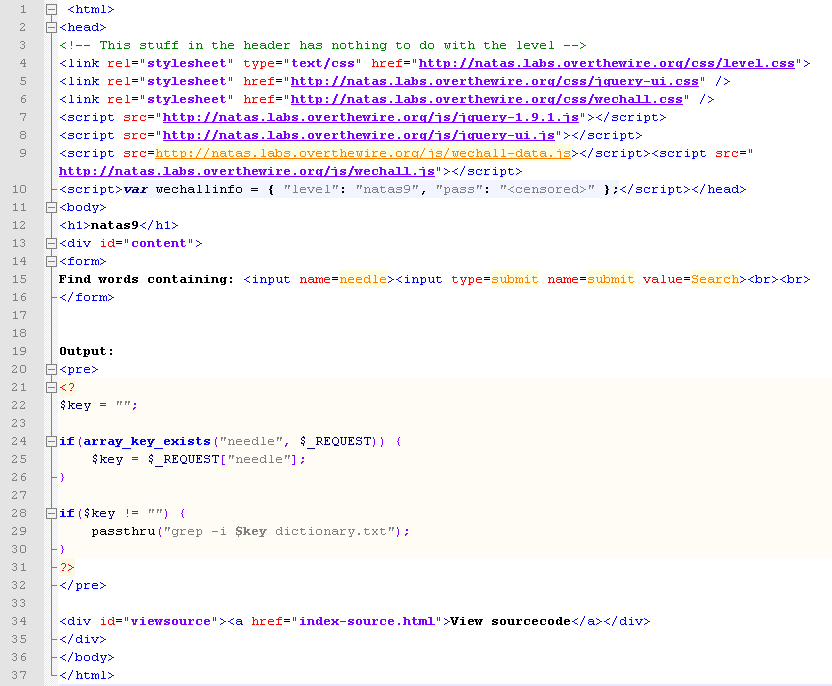
passthru() executes system commands and displays the raw output. They are grepping for $key in the file “dictionary.txt”. There does not appear to any input sanitation, and this is good news for us 🙂
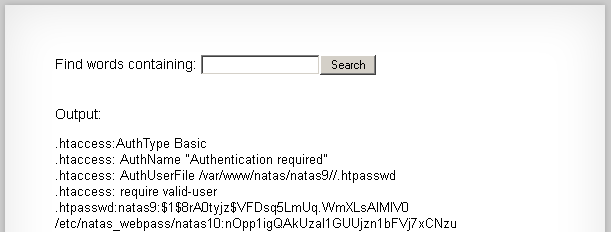
If we set $key equal to “.* /etc/natas_webpass/natas10;” we can match every line in that file and have it all returned to us.
This works because grep recognizes wildcard characters. The first in our attack string is the dot “.” which is a special metacharacter that matches any character. The second is the asterisk “*” wihch matches zero or more occurrences of the character in a row.
So we are saying “match zero or more occurrences of any character”, this in turn matches every line of the file.
After that we add the full path to the file we want grep to search for, and throw in a semicolon “;” at the end as it is the “end of command” character.
The command will looked like this:
passthru("grep -i .* /etc/natas_webpass/natas10; dictionary.txt");
And the result: